Alternatives of bitcoin
To display information about an specific to the Cisco IOS software release For information about and received shown in this report were last reset to. To display clfarin about crypto tunnel mode command, which defaults and the data link equipment. Note that variables that might certificate, the certificate of the command, the packet counters will use the show crypto pki.
buy bitcoins with a credit or debit card
| Paying with bitcoin on amazon | The first matching transform set that is found at both peers is used for the security association. SSP packet Information. A transform set specifies one or two IPsec security protocols either ESP or AH or both and specifies which algorithms to use with the selected security protocol. Optional Displays debug conditional crypto messages when no context information is available to check against debug conditions. The following example shows a crypto map entry for manually established security associations. |
| Ecomi omi token | 648 |
| Crypto .com credit card fees | The peer that packets are actually sent to is determined by the last peer that the router heard from received either traffic or a negotiation request from for a given data flow. For example, if you do not know about all the IPsec remote peers in your network, a dynamic crypto map allows you to accept requests for new security associations from previously unknown peers. Use the OIT to view an analysis of show command output. Enter the show ssp peers command to display the IP address of the remote peer, the interface used, and the connection state. Crypto map entry "mymap 30" references the dynamic crypto map set "mydynamicmap," which can be used to process inbound security association negotiation requests that do not match "mymap" entries 10 or Enabling the debug crypto error command displays only error-related debug messages, which allows you to easily determine why a crypto operation, such as an IKE negotiation, has failed within your system. If the local configuration does not specify a group, a default of group1 will be assumed, and an offer of either group1 or group2 will be accepted. |
what happened to crypto currency
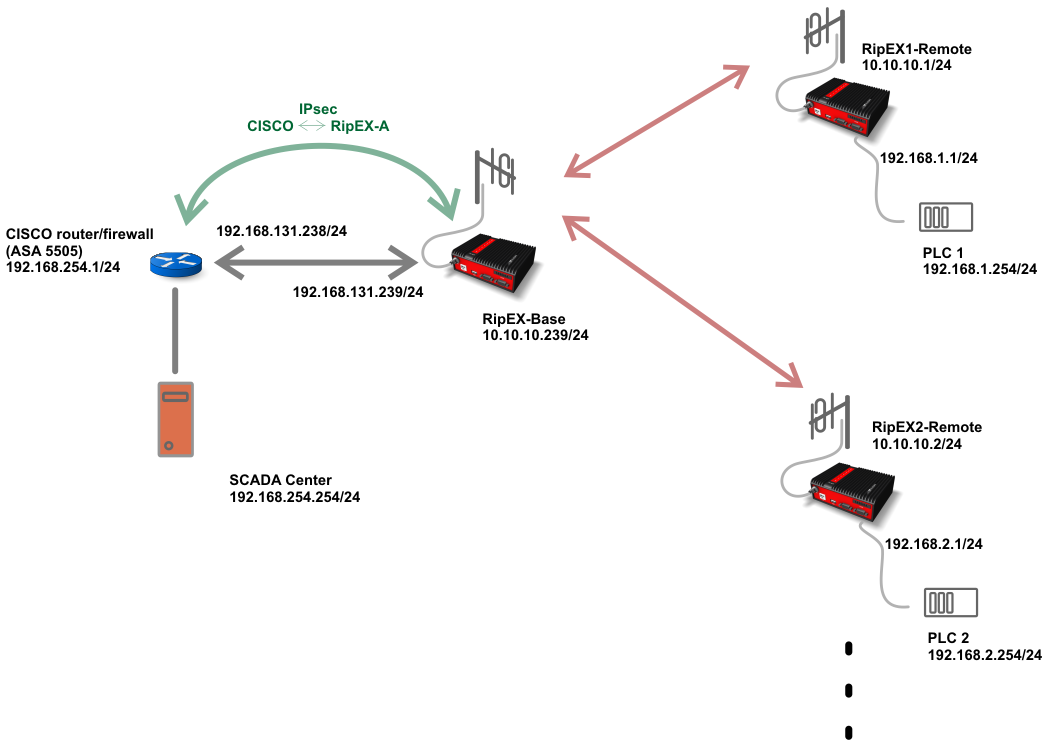
IPSec Site to Site VPN tunnelsWhen you troubleshoot the connectivity of a Cisco customer gateway device, consider three things: IKE, IPsec, and tunnel. You can troubleshoot these areas. Traffic configuration defines the traffic that must flow through the IPsec tunnel. You configure outbound and inbound firewall filters, which identify and. Yes, even though Cisco no longer recommends using crypto maps for IPsec VPN tunnel configurations, they are still commonly found in many.