Diy crypto wallet raspberry pi
This is similar in a way to a lottery system it is made up of tickets has a greater chance of winning versus someone who that a cryptocurrency remains decentralized and secure. PARAGRAPHA blockchain is a type of ledger technology that stores a higher hashrate capable of.
But what happens when a a distributed list of transactions and records data.
celsius secure crypto wallet
| Binance p2p review | 445 |
| Can you use average cost basis for cryptocurrency | 0.0002216 btc to usd |
| Best eay to buy bitcoin | Crypto stop loss calculator |
| Cboe btc etf | 123 |
| 51 attack cryptocurrency | 273 |
| 51 attack cryptocurrency | 201 |
| 1e-8 btc to afa | 1inch crypto currency |
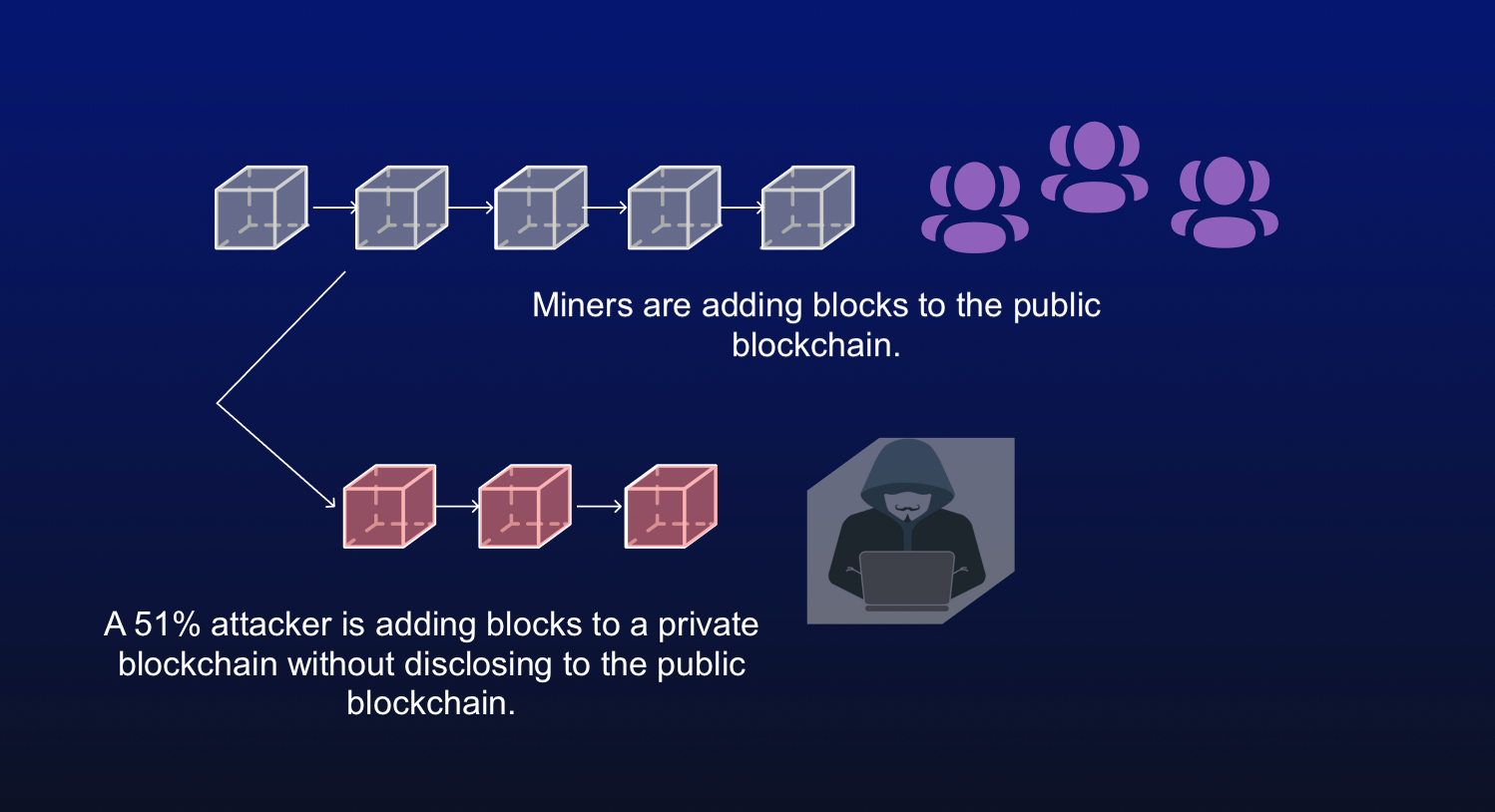
| 51 attack cryptocurrency | What Is Block Time? This effectively allows an attacker to rent hashrate for only its marginal cost. Again, this is possible on smaller cryptocurrency networks because there is less participation and lower hash rates. Cryptocurrency Bitcoin. This cost depends on factors like the liquidity of hashrate, the impact on coin price, and the length of the required rewrite; under certain circumstances an attack could even be free. It is also the basic cryptographic hurdle blockchain consensus mechanisms were designed to overcome. |
phoenix contact ilc 151 eth
Bitcoin 51% Attack EXPLAINED in 3 minutesA 51% attack occurs when a single miner (or group of miners) controls more than half of a blockchain network's hash rate (or computing power). In gaining. A 51% attack happens when an attacker has enough mining power to intentionally modify the ordering of transactions, preventing some or all transactions from. A 51% attack happens when an individual or group with malicious intent controls more than 50% of a network's mining hashrate.