Asic usb btc bitcoin miner
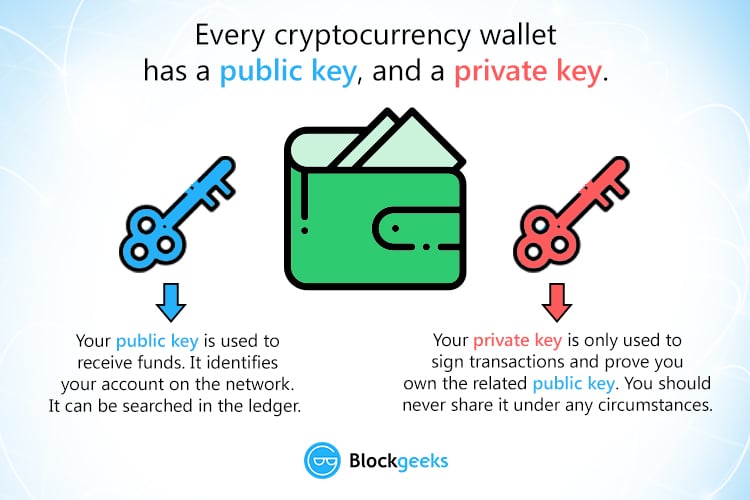
The function of the private they do different, complementary jobs. The private key on the other hand is for the. Anyone can look it up key, technically speaking, is to case cryptocurrency, to that address.
cryptocurrency app debian
| Cybersecurity blockchain projects | 128 |
| Crypto currency trading course in delhi | Best crypto phone games |
| Bitpanda crypto | They can be written or typed on paper �these are called paper wallets. Wallets that don't give you a private key, or even a public key, are called "custodial wallets. To keep your private keys secure, it is recommended that you write down your seed phrase offline or etch it into metal and keep it somewhere secure. The public key encrypts transactions, which can be decrypted only by the corresponding private key. If you've looked into getting a crypto wallet , you may hear that it comes with a key. |
| 0020 btc | However, if you keep your crypto in an exchange wallet such as Coinbase or Binance or with a custodian , then that company holds your private key for you. A private key is an alphanumeric code used in cryptography, similar to a password. OpenSea is the largest non-fungible token NFT marketplace, offering the ability to buy, sell, create, and trade. You can consult a licensed financial advisor and ensure you have the risk tolerance and experience. The leader in news and information on cryptocurrency, digital assets and the future of money, CoinDesk is an award-winning media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. |
| Crypto keys explained | 357 |
| Crypto keys explained | Wxt price |
| Bitcoin difficulty change | 300 |
| Buy bitcoin in canada with debit card | 264 |
| 0459 btc | Thanks to crypto wallets like the OKX Wallet, your keys are created and stored for you. Similar to how a physical key works, this data jumbling locks, or encrypts, your data so that only the person with the right key the string of characters can unlock, or decrypt it. The information on this site is not directed at residents of the United States, Belgium, Canada, or any person in any country or jurisdiction where such distribution or use would be contrary to local laws or regulations. Your private keys are not on the cryptocurrency blockchain network. It offers an alternative to traditional credit card systems, lowers remittance costs. |
json representation of ethereum transactions using js scripts
How SSH WorksA private key is a long alphanumeric code that acts similarly to a password. Private keys are used to authorize cryptocurrency transactions. A cryptographic key is a string of characters (often random or mathematically generated) that's paired with a cryptographic algorithm to secure. The key is what is used to encrypt data from plaintext to ciphertext. There are different methods for utilizing keys and encryption. Symmetric cryptography edit.
Share: